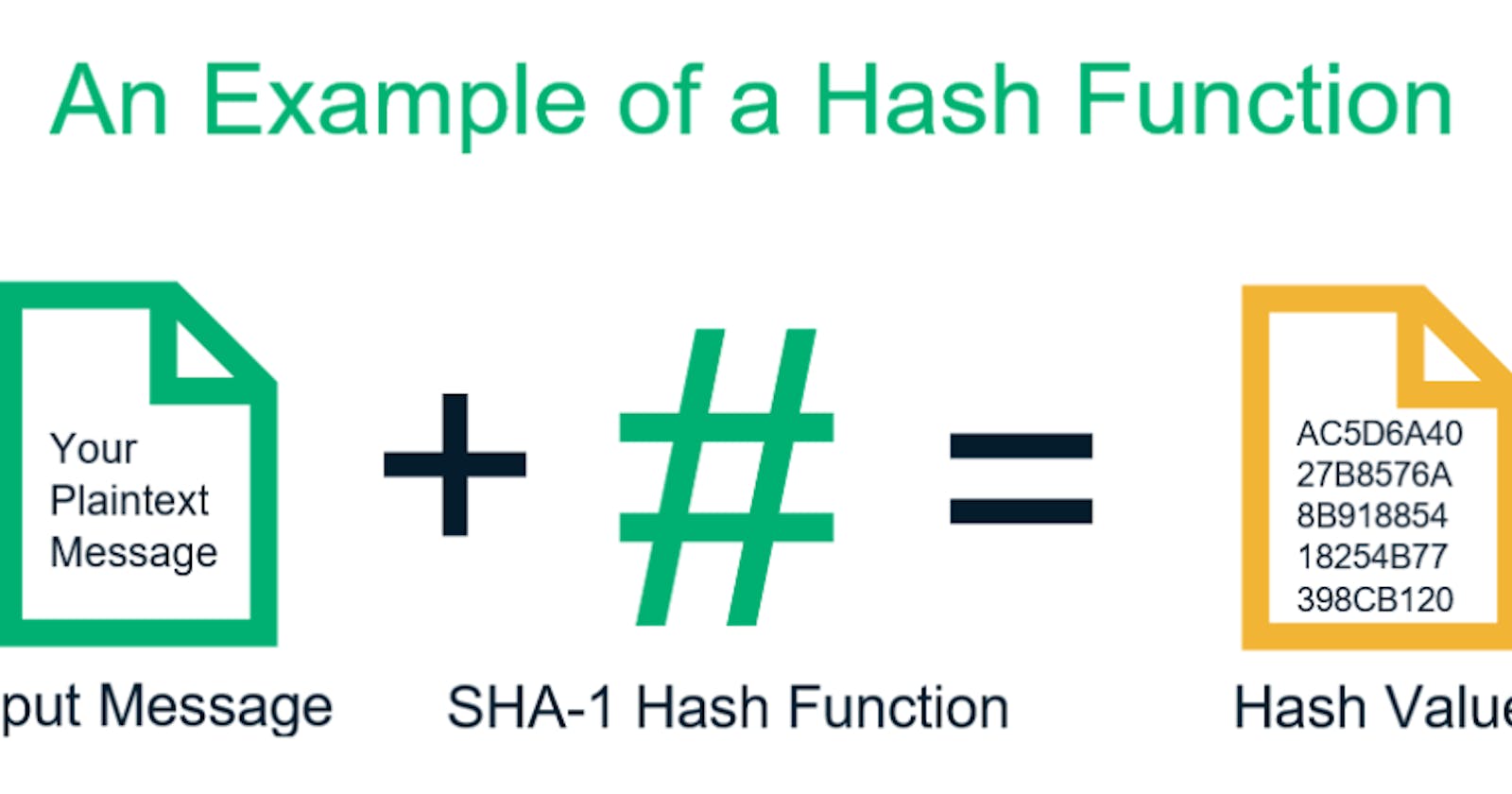
SHA-1 is a popular heuristic hash function that is currently in vogue. In this experiment, we shall familiarize ourselves with SHA-1 as well as look at one important application of hashing, namely, the HMAC algorithm which is currently used in the Internet to achieve data integrity
Secure Hash Algorithms The following list describes the most common Secure Hash Algorithms (SHAs): • SHA-0: This is a 160-bit function introduced by NIST in 1993.
• SHA-1: SHA-1 was introduced in 1995 by NIST as a replacement for SHA-0. This is also a 160-bit hash function. SHA-1 is used commonly in SSL and TLS implementations. It should be noted that SHA-1 is now considered insecure, and it is being deprecated by certificate authorities. Its usage is discouraged in any new implementations.
• SHA-2: This category includes four functions defined by the number of bits of the hash: SHA-224, SHA-256, SHA-384, and SHA-512.
• SHA-3: This is the latest family of SHA functions. SHA-3-224, SHA-3-256, SHA-3-384, and SHA-3-512 are members of this family. SHA-3 is a NIST-standardized version of Keccak. Keccak uses a new approach called sponge construction instead of the commonly used Merkle-Damgard transformation.
• RIPEMD: RIPEMD is the acronym for RACE Integrity Primitives Evaluation Message Digest. It is based on the design ideas used to build MD4. There are multiple versions of RIPEMD, including 128-bit, 160-bit, 256-bit, and 320-bit.
• Whirlpool: This is based on a modified version of the Rijndael cipher known as W. It uses the Miyaguchi-Preneel compression function, which is a type of one-way function used for the compression of two fixed-length inputs into a single fixed-length output. It is a single block length compression function.
ONLINE SIMULATOR USED: Google Colab
Task 1: Implement python code for encryption and decryption
Code 1
import hashlib
m=hashlib.sha256()
m.update(b"My name is PAVANDEEP KAUR")
m.update(b"and my UID is 17bcs4521")
m.digest()
 Code 2
Code 2
from hashlib import blake2b
h=blake2b()
h.update(b'Internet of things Is EverywherE')
h.hexdigest()
 Code 3-Using different digest sizes
Code 3-Using different digest sizes
BLAKE2 has configurable size of digests up to 64 bytes for BLAKE2b and up to 32 bytes for BLAKE2s. For example, to replace SHA-1 with BLAKE2b without changing the size of output, we can tell BLAKE2b to produce 20-byte digests:
from hashlib import blake2b
h = blake2b(digest_size=20)
h.update(b'Replacing SHA1 with the more secure function')
h.hexdigest()
h.digest_size
 Task 2: Create Hash functions (SHA) using online simulator
Task 2: Create Hash functions (SHA) using online simulator
ONLINE SIMULATOR USED: xorbin.com/tools/sha256-hash-calculator