What is Diffie Hellman protocol?
As the name suggests, this algorithm is used to exchange the secret key between the sender and the receiver. This algorithm facilitates the exchange of secret key without actually transmitting it.
STEPS OF PROCEDURE:
STEP 1 : Firslty, choose a large prime number p and a generator g for that prime.
STEP 2 : Secondly, both Alice and Bob generate their respective keys A and B. And (ga,gb) for their keys respectively.
STEP 3 : Both Alice and bob send exchange their ga,gb.
STEP 4 : Finally, both calculate their public keys gab and gba repectively.
STEP 5 : If both gab and gba are equal then Deffie-Hellman key exchange is verified.
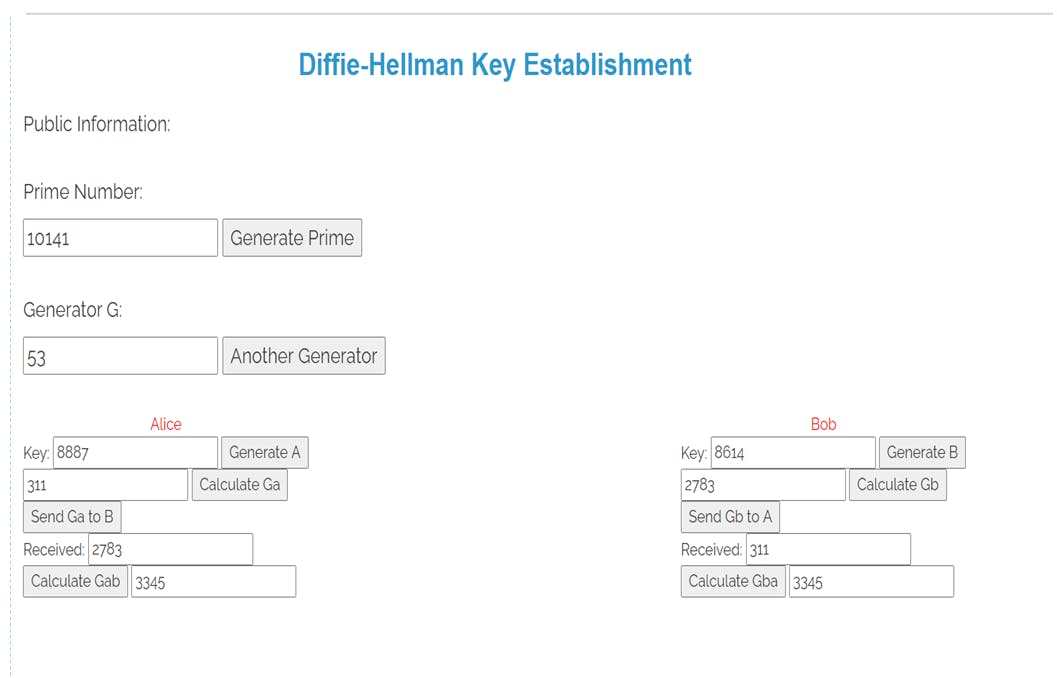
Here both gab and gba are equal. Hence, Deffie-Hellman key exchange is verified.
