Think before you click. Secure your cyberspace, secure your digital life
Hey there !! In this article, you will get to know about some cyberattacks in simple terms. So, let's start ....
Man in the Middle attack
Suppose a person sends a request to an application. But hacker as middle person manipulates the conversation and retrieves confidential information. It is known as Man-in-the-middle attack or MiTM. So, in very simple terms, MitM attack occurs when a communication between two systems or people is intercepted by an unauthorized party.
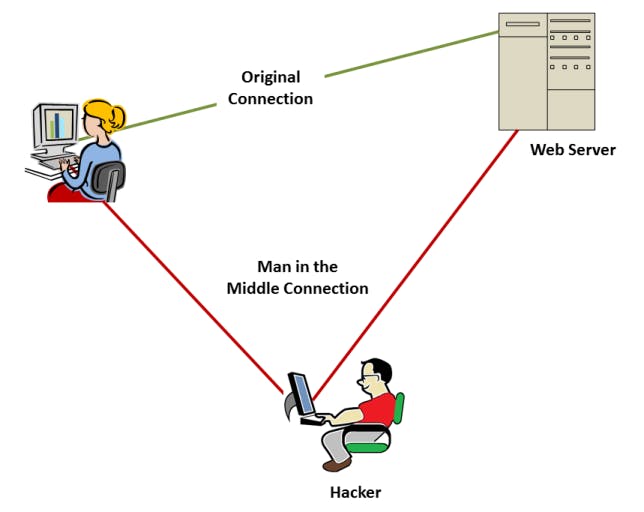
Image from Comodo Antivirus
Phishing attack
Phishing attack is done via emails to steal sensitive information like login credentials or credit card information. And it seems like emails are coming from legitimate source but they are not.
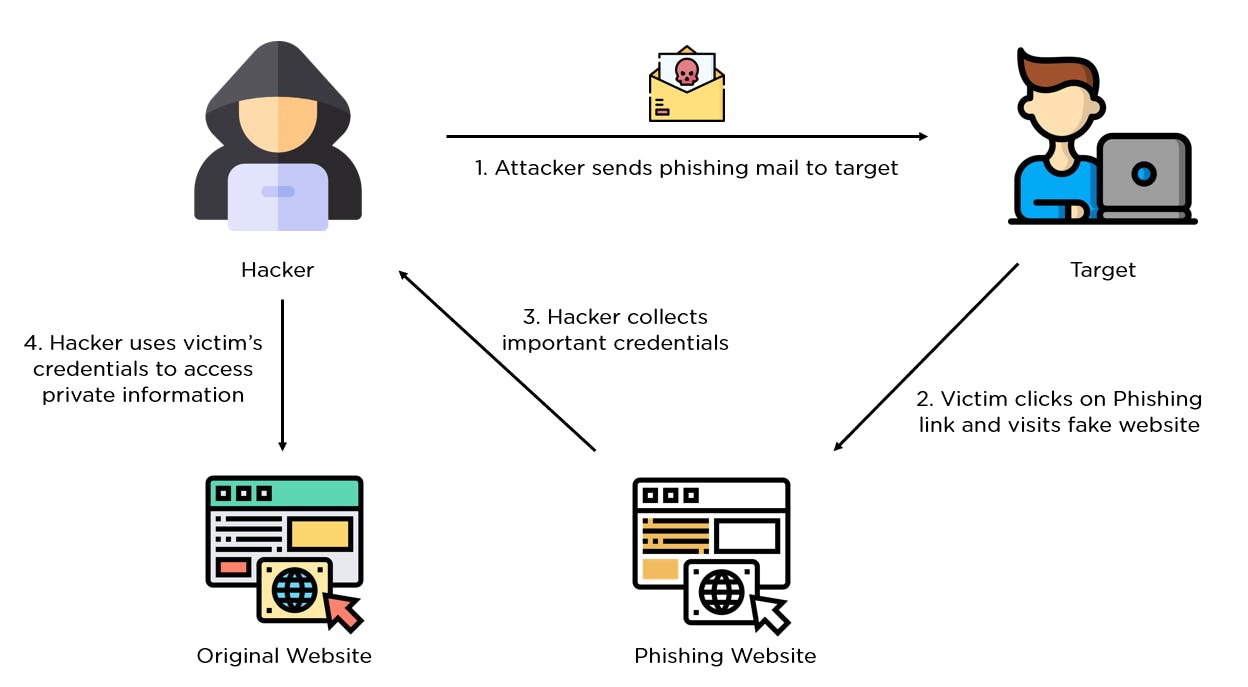
Image from Simplilearn
Spoofing attack
Spoofing attacks copy and exploit the identity of your contacts, the look of well-known brands, or the addresses of trusted websites. Some attackers disguise their communications, such as emails or phone calls — so that they appear to be coming from a trusted person or organization. With these types of spoofing attacks, hackers try to trick you into exposing sensitive personal information.
The difference between spoofing and phishing is that while spoofing uses someone else’s identity, phishing attacks try to access sensitive information.
DOS attack
Denial of Service or DOS attack is an attack made to shut down a system, so that the system will no more accessible to the user. It is done by flooding the target with traffic.
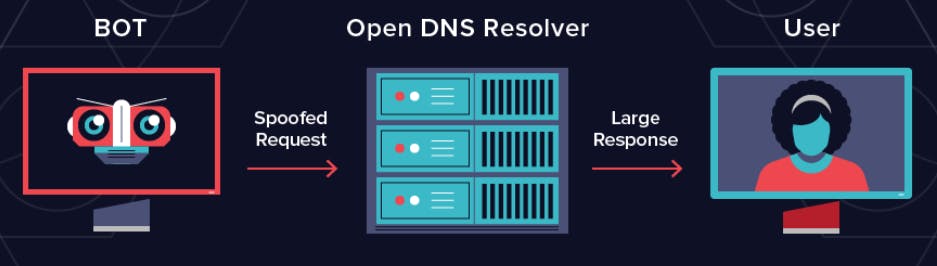
DNS Amplification attack
Attackers are attacking the DNS server directly and requesting a large amount of data back from the DNS server, which can bring the DNS server down and cripple anyone that is using that DNS server for name resolution services.
Image from Varonis
Smurf attack
It is a kind of DDOS attack in which an attacker attempts to flood a targeted server with ICMP packets by making requests with spoofed IP address.
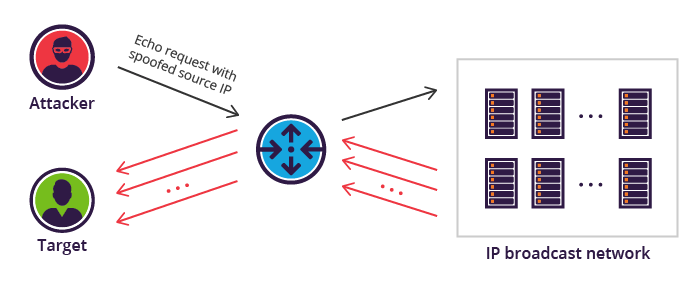
Image from Imperva
SQL Injection attack
Hackers perform an SQL injection attack through an entry field — such as a login portal, or a search bar — in a web API. By altering the entry data with a malicious snippet of code known as an exploit, a cybercriminal can trick an unsecured database into interpreting the data as a command.
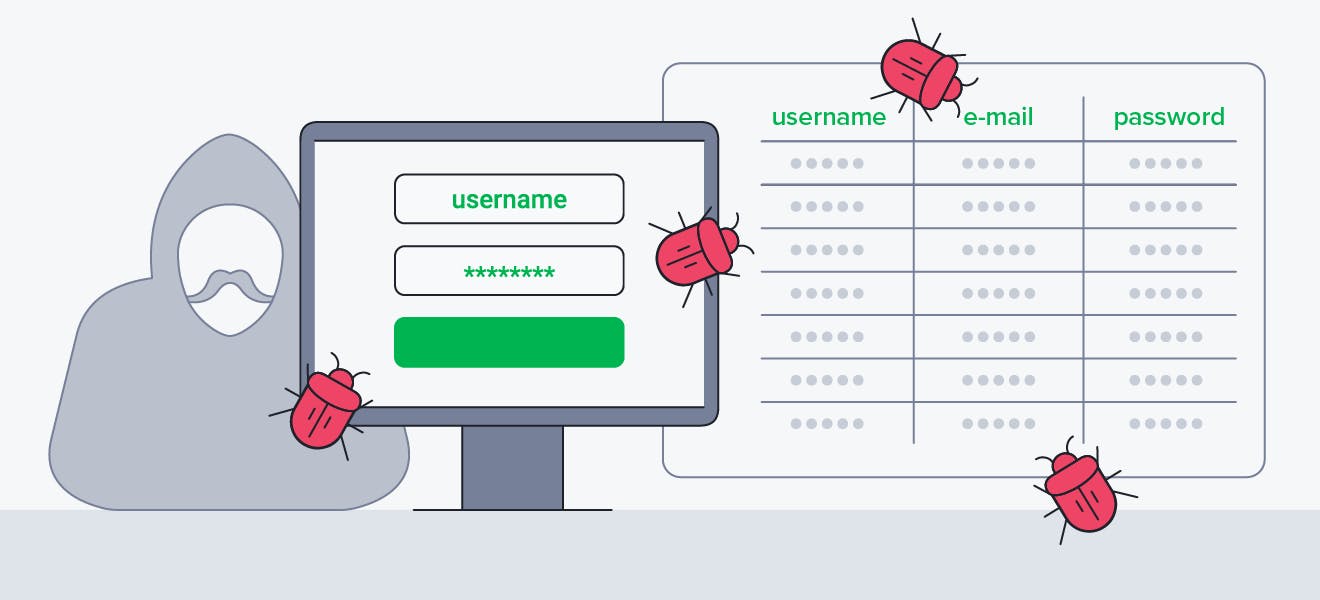
Image from AVG
Brute-Force attack
It is an trial and error attack to guess login credentials. Brute force attacks run every single combination of numbers and characters available, so irrespective of how secure user credentials are, given the time and processing power, they will get cracked.
Cross site scripting (XSS)
In this attack, code is executed in the victims browser either from injecting JavaScript into a web application and having a victim visit the vulnerable URL.
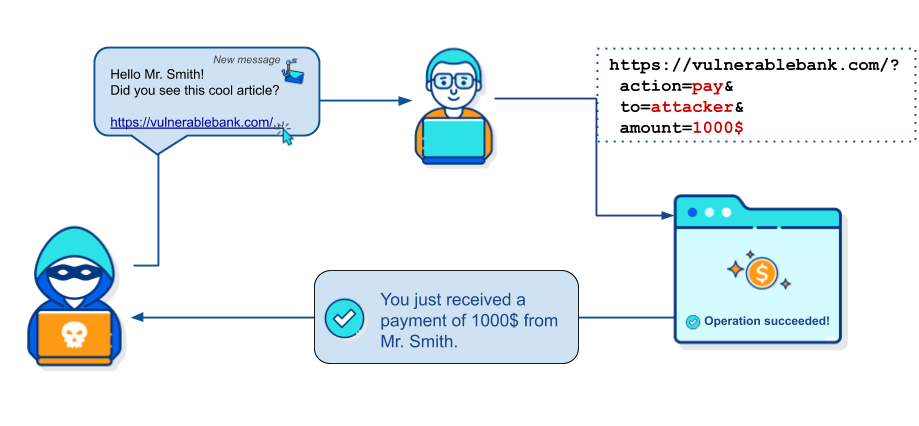
Image from Secure Flag Knowledge Base
Zero Day attack
The typical zero-day attack, by definition, exploits software flaws before they are publicly disclosed. Stuxnet is a computer worm that affected the computers in Iran’s nuclear plant Natanz back in 2010. This malware exploited a zero day vulnerability in Windows at that time.
Ping of Death
A Ping of death (PoD) attack is a denial-of-service (DoS) attack, in which the attacker aims to disrupt a targeted machine by sending a packet larger than the maximum allowable size, causing the target machine to freeze or crash.
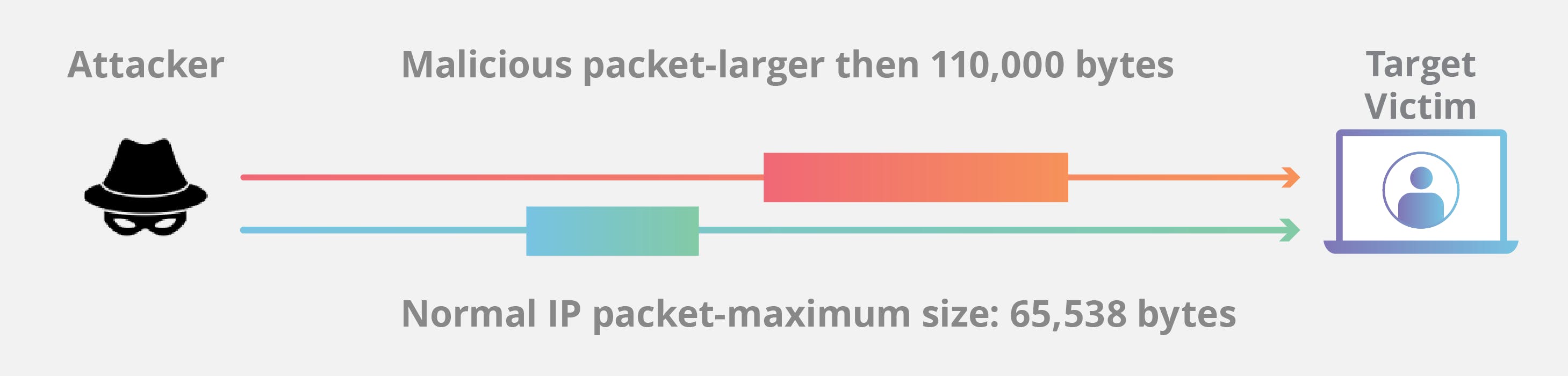
Image from Cloudflare
Social Engineering attack
It includes urgent voice mails convince victims they need to act quickly to protect themselves from arrest or other risk.
EXAMPLE - You receive an email from customer support at an online shopping website that you frequently buy from telling you that they need to confirm your credit card information to protect your account. The email language urges you to respond quickly to ensure that your credit card information isn’t stolen by criminals. Without thinking twice and because you trust the online store, you send not only your credit card information but also your mailing address and phone number. A few days later, you receive a call from your credit card company telling you that your credit card has been stolen and used for thousands of dollars of fraudulent purchases.
Whaling attack
It is a type of Phishing attack that targets high level executives or we can say senior management in an organization such as CEO, CFO, to steal sensitive information from the company.
Eavesdropping
Hackers are eavesdropping on your communications seeking to steal login credentials, and other sensitive information on a user’s devices. Eavesdropping also allows hackers to listen into VoIP communications as well. Eavesdropping is similar to a sniffing attack, where software applications allow a hacker to steal usernames and passwords simply by observing network traffic. This often happens on Public Wi-Fi networks.
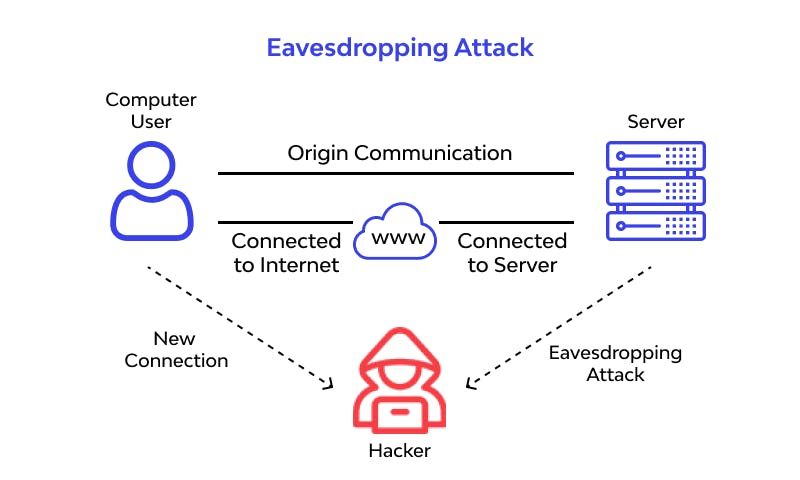
Image from Wallarm
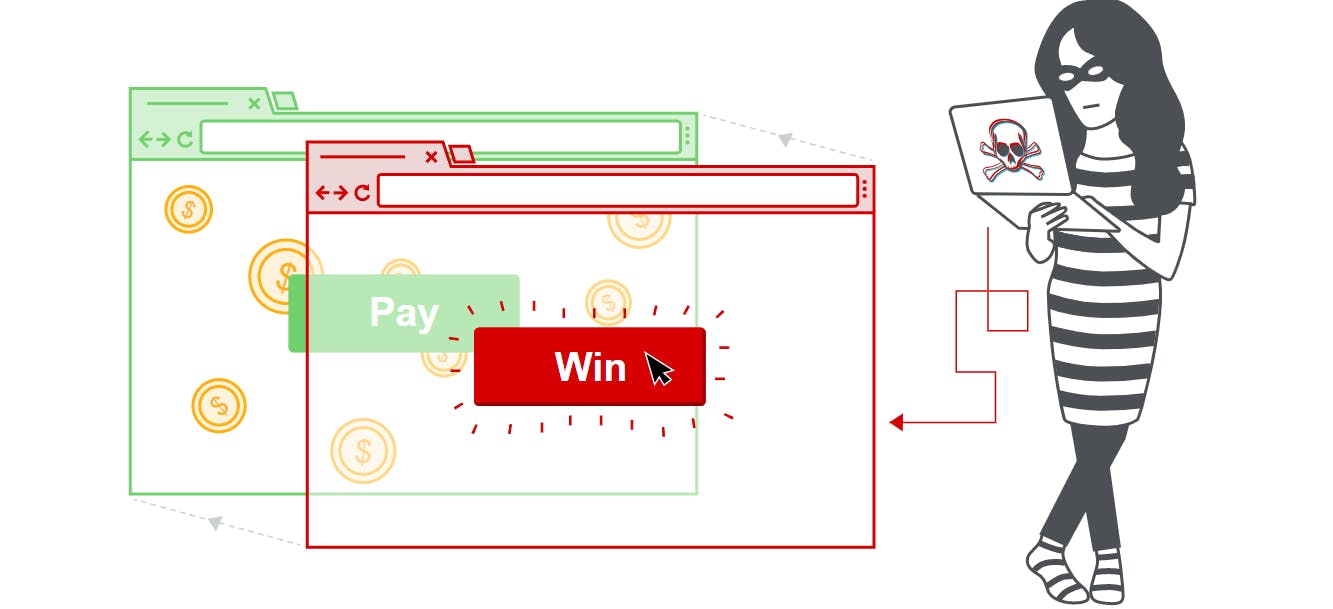
Click-jacking attack
Clickjacking is an interface-based attack in which a user is tricked into clicking on actionable content on a hidden website by clicking on some other content in a decoy website. Consider the following example:
A web user accesses a decoy website (perhaps this is a link provided by an email) and clicks on a button to win a prize. Unknowingly, they have been deceived by an attacker into pressing an alternative hidden button and this results in the payment of an account on another site. This is an example of a clickjacking attack.
Image from PortSwigger
Wrap Up
Keep your personal information safe—choose disk encryption, strong passwords, and 2-step verification🔒. Putting your best foot forward and taking a proactive stance against cybersecurity threats is the best defense.